In order to run the examples presented in IT Wonder Lab, you will need programmatic access to the AWS Cloud API.
The following instructions guide you on creating a user for programmatic access with full administration permissions.
How To Create an AWS IAM User for Demos
Sign in AWS Management Console
Sign in to the AWS Management Console using the email address of your new AWS account.
Access AWS IAM Service for user management
Select "IAM Manage User Access and Encryption Keys" in the AWS Console.
Create a user in the AWS IAM Management Console
Follow the the Add User wizard.
Use the newly created users for Terraform
Check the Tutorial on How to create AWS IAM users using Terraform.
Be aware that these instructions should only be used for demos and accounts should be disabled after completion.
These instructions don't follow the common security practice of Granting Least Privilege.
In other tutorials, we will show how to properly manage security in the cloud.
Sign in to the AWS Management Console using the email address of your new AWS account created on the Create an AWS Account for Demos post.
Fill in the e-mail address and press Next.
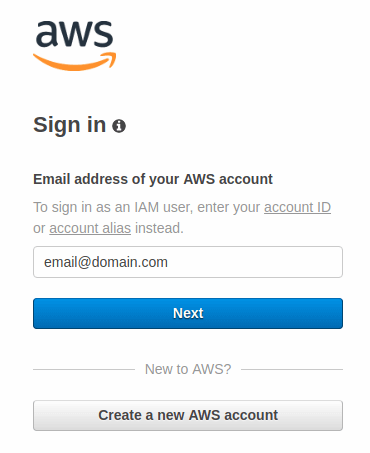
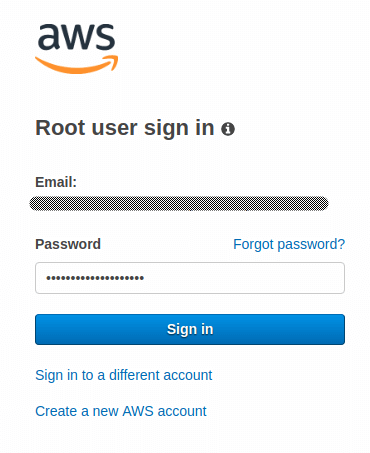
Fill in the password and press Sign in.
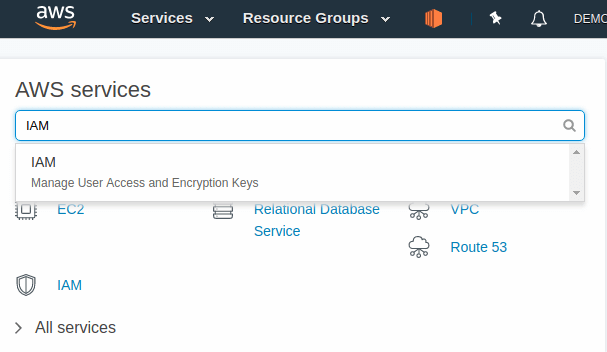
On the AWS Management Console home, write IAM into the search box and select "IAM Manage User Access and Encryption Keys"
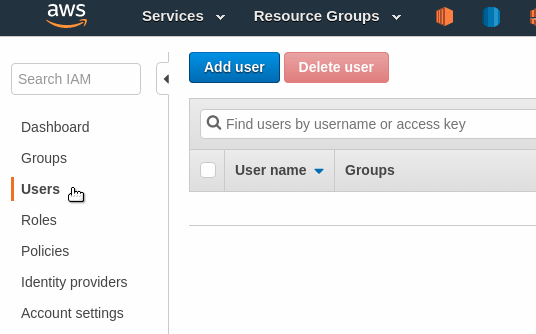
Click Users on the left menu and click the Add User button.
AWS shows a user creation wizard.
AWS IAM Add User: Add tags.
In current releases of the AWS console, the Add User wizard has been updated to include a new step to Add Tags to the created user. That step is not shown in this tutorial screenshots.
First, write a user name.
We like to follow a pattern for all the elements in the infrastructure, since users are part of the infrastructure, start them with a prefix that uniquely identifies this Cloud.
In this case, the prefix will be ditwl which stands for Demo IT Wonder Lab in lowercase. Append the name of the user or a functional description, in our case, the full user name will be ditwl-terraform-user.
AWS allows two types of user access:
Since we are creating a user for Terraform to access the AWS API, select Programmatic access for the AWS access type.
Click Next: Permissions
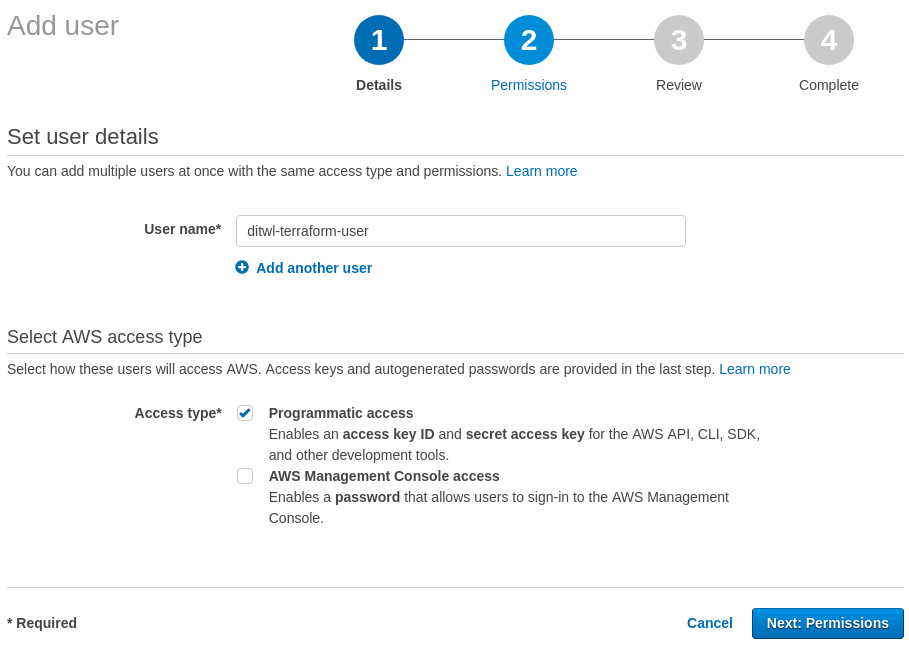
The recommended way to manage user permissions is by assigning users to groups and giving permissions to the groups. Since this is our first user (beyond the root account), press Create group to create our first group.
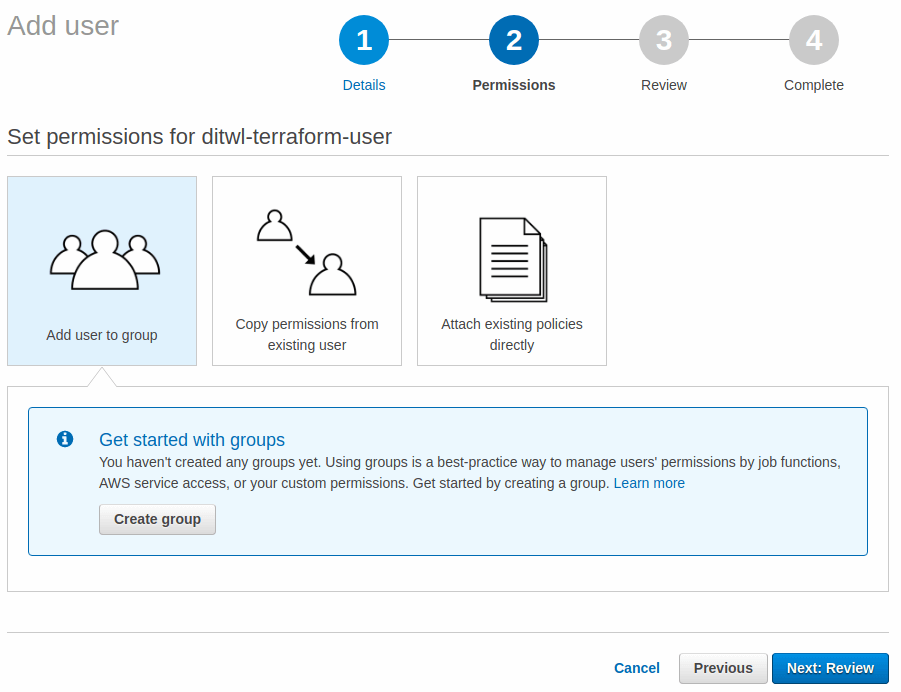
A new form is shown for the Create group. Name the group (we will use ditwl-admins as the name) and select AdministratorAccess as the Policy. The AdministratorAccess provides full access to AWS services.
Press Create Group to go back to the previous screen.
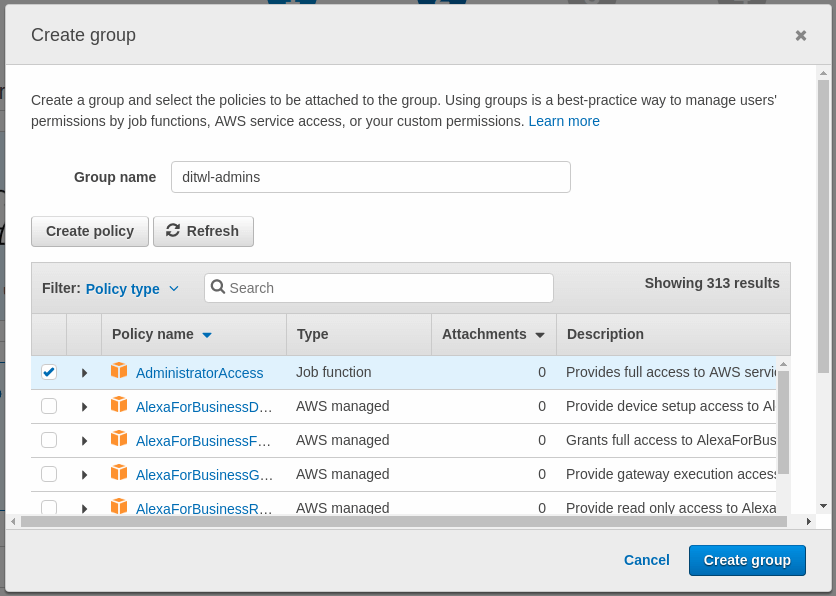
Assign the previously created group to the user and click Next: Review.
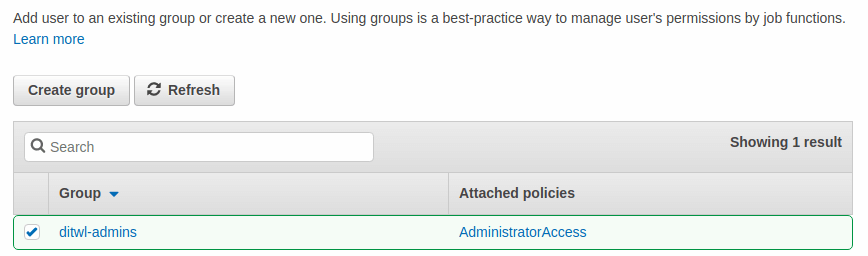
The review screen shows all the data for the user. Review the correct spelling of the names and group assignments and press Create user.
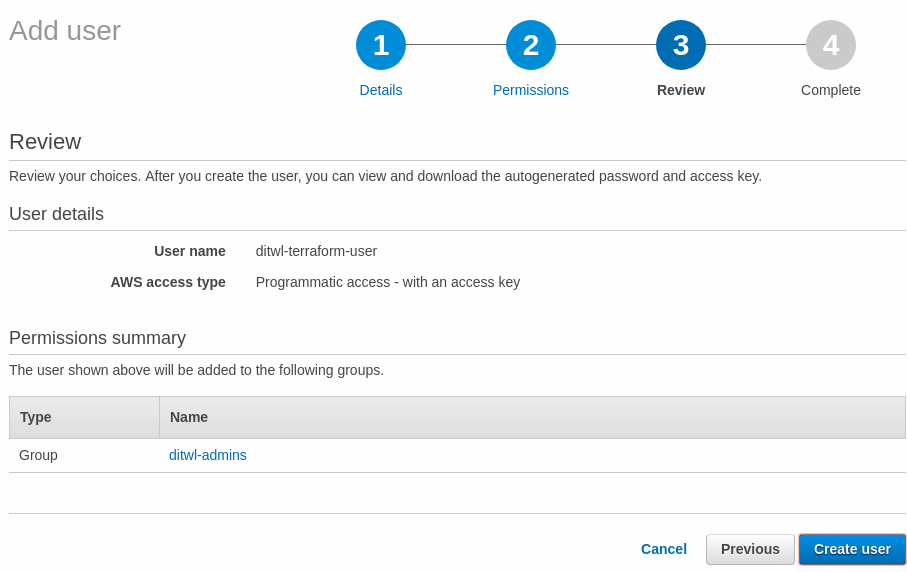
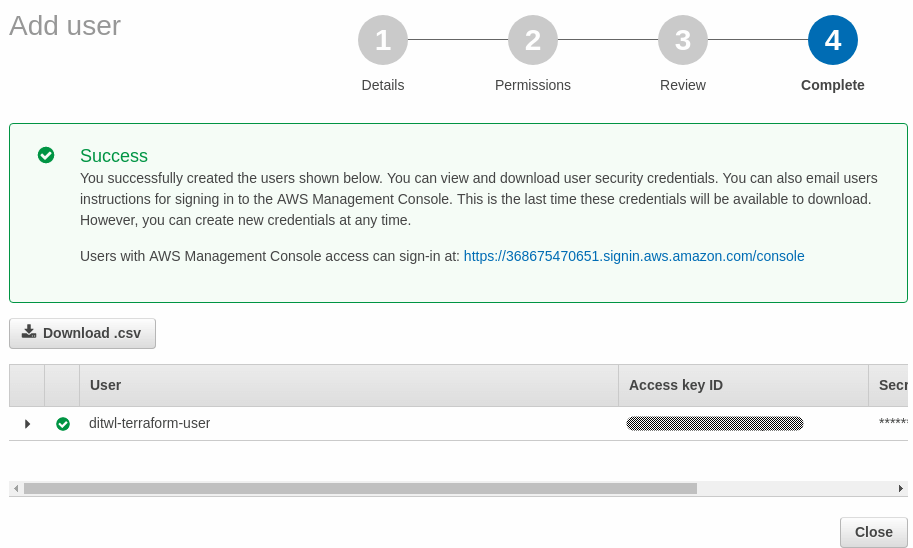
The user has been created and AWS shows the Access key ID and the Secret access key. This is the only time that AWS will show the Secret access key.
Press Download .csv to download a CSV file named credentials.csv that contains the credentials or press Show to see the Secret access key on the screen.
The downloaded file credentials.csv contains the following fields [1]:
User name,Password,Access key ID,Secret access key,Console login link ditwl-terraform-user,,A1B2C3D4E5F6G7H8I9J0,QwertYuiopASDFGHJKL123456789sadfghjkvcbn,https://134567891011.signin.aws.amazon.com/console
Keep the credentials safe by storing them under encryption and make sure that you don't upload the Secret access key to a public repository. The Access Key ID and Secret access key can be used to buy services from AWS that will be charged to your account.
1] The Access Key ID, Secret access key, and Console login link shown in the example are fake.
Use your newly created user for Terraform and OpenTofu creation of AWS Infrastructure, like:
Explore other AWS Tutorials.

IT Wonder Lab tutorials are based on the diverse experience of Javier Ruiz, who founded and bootstrapped a SaaS company in the energy sector. His company, later acquired by a NASDAQ traded company, managed over €2 billion per year of electricity for prominent energy producers across Europe and America. Javier has over 25 years of experience in building and managing IT companies, developing cloud infrastructure, leading cross-functional teams, and transitioning his own company from on-premises, consulting, and custom software development to a successful SaaS model that scaled globally.
Are you looking for cloud automation best practices tailored to your company?