Using the Terraform aws_route53_delegation_set, aws_route53_zone, and aws_route53_record resource blocks to configure DNS in AWS.
Welcome to our tutorial series where we dive into cloud infrastructure deployment using Terraform or OpenTofu on AWS. In this series, the fundamentals are shown, guiding you through the process of minimizing resource usage and simplifying the deployment complexities associated with cloud infrastructure. This tutorial series is a work in progress.
This comprehensive OpenTofu and Terraform tutorial guides you step-by-step through creating infrastructure in AWS using Terraform.
Infrastructure as Code (IaC) helps maintain consistency, enables version control, enhances collaboration among teams, allows for easier replication of environments, streamlines the deployment and management of infrastructure boosting efficiency, and reducing errors in managing complex systems.
How to start building AWS infrastructure with Terraform: Route 53
Read previous sections of the tutorial: AWS with Terraform Tutorial
Amazon Route 53 is a scalable and highly available Domain Name System (DNS) web service provided by Amazon Web Services (AWS). It is designed to route end-user requests to globally distributed endpoints, such as web applications or resources, and effectively connects user requests to the corresponding AWS resources.
Definition of Route 53 DNS Servers and Records with Terraform
A Route 53 delegation set is a set of four authoritative name servers created for a hosted zone in Amazon Route 53, In AWS DNS Resolver, private DNS queries take precedence over public DNS queries. DNS Zones are created using the Terraform resource block aws_route53_zone. DNS Records are created using the Terraform resource block aws_route53_record.
Plan, and apply the Terraform plan to select the AWS AMI.
AWS charges for each hosted zone the number of monthly queries to the zone
Common Questions About AWS Route 53
Can Terraform manage Route 53 health checks and failover configurations?, How do I update existing DNS records with Terraform without causing downtime?, Should private records be stored in public Route 53 zones?, How can I use Terraform to configure Route 53 for domain registration and DNS hosting?
Other tutorials for creating infrastructure in AWS using Terraform
Read previous sections of the tutorial:
Amazon Route 53 is a scalable and highly available Domain Name System (DNS) web service provided by Amazon Web Services (AWS). It is designed to route end-user requests to globally distributed endpoints, such as web applications or resources, and effectively connects user requests to the corresponding AWS resources.
AWS offers domain registration and also DNS Service for domains registered outside AWS. For simplicity, we will use Amazon Route 53 as a DNS Server for a subdomain of an already registered domain name.
The tutorial defined two zones, a public zone to be used for public instance ditwl-ec-front-end-001 registration, and a private zone that will be used for internal hostname resolution.
The DNS diagram shows the different DNS Zones and the registration of the hosts.
Previous sections of this AWS with Terraform guide have covered basic information about Terraform and AWS and have configured and used the AWS Terraform provider to create a VPC, four subnets, one Internet Gateway, two NAT Gateways, three Routing Tables, Security Groups, and a Private Key.
Add the following blocks to the terraform-aws-tutorial.tf created in previous sections.
A Route 53 delegation set is a set of four authoritative name servers created for a hosted zone in Amazon Route 53. These name servers are assigned to a hosted zone and are responsible for answering DNS queries for that zone. Delegation sets are used to delegate authority for a domain's DNS to Route 53, allowing Route 53 to manage DNS records and respond to queries on behalf of that domain. This delegation enables efficient management and distribution of DNS information for the domain across multiple name servers.
The assigned four authoritative name servers will be used to delegate the subdomain to Amazon Route 53. Delegation sets are mostly used for public zones, usually created once and re-used across Terraform plans to avoid having to update the delegation to the four authoritative name servers in other name servers or registrars.
Route 53 Delegation Sets are created using terraform resource block aws_route53_delegation_set.
# Route53 Delegation Set
resource "aws_route53_delegation_set" "ditwl-r53ds-001" {
reference_name = "ditwl-r53ds-001"
}Two DNS Zones are created:
demo.itwonderlab.com" that uses the delegation set ditwl-r53ds-001.demo.itwonderlab.local" assigned to the VPC ditlw-vpc. (VPC-assigned zones are internal and act as private DNS zones and can only be queried inside the VPC).In AWS DNS Resolver, private DNS queries take precedence over public DNS queries. This means that if a DNS query is made for a domain name that exists in the private hosted zone associated with the VPC, the resolver will resolve the query using the private DNS records. If the domain name doesn't exist in the private hosted zone, only then will the resolver look for public DNS records. This approach helps ensure that private resources within a VPC are resolved using the appropriate private DNS configuration before attempting to resolve public DNS records.
DNS Zones are created using the Terraform resource block aws_route53_zone.
# Route53 Public Zone (*.demo.itwonderlab.com)
resource "aws_route53_zone" "ditwl-r53-public" {
name = "demo.itwonderlab.com"
delegation_set_id = aws_route53_delegation_set.ditwl-r53ds-001.id
tags = {
Name = "ditwl-r53-public"
}
}
# Route53 Private Zone (*.demo.itwonderlab.local)
resource "aws_route53_zone" "ditwl-r53-private" {
name = "demo.itwonderlab.local"
vpc {
vpc_id = aws_vpc.ditlw-vpc.id
}
tags = {
Name = "ditwl-r53-private"
}
}A DNS record is created for each instance using its private and public (only available for instances in public subnets).
Public records created in the Public zone ditwl-r53-public serving the demo.itwonderlab.com subdomain:
ditwl-r53-public serving the demo.itwonderlab.com subdomain.Private records created in the Private zone ditwl-r53-private serving the demo.itwonderlab.local subdomain:
DNS Records are created using the Terraform resource block aws_route53_record.
# Public A DNS Record: Front-end server (ditwl-ec-front-end-001)
resource "aws_route53_record" "ditwl-r53-public-front-end-001" {
zone_id = aws_route53_zone.ditwl-r53-public.id
name = aws_instance.ditwl-ec-front-end-001.tags["public_name"]
type = "A"
ttl = "300"
records = [aws_instance.ditwl-ec-front-end-001.public_ip]
}
# Private A DNS Record: Front-end server (ditwl-ec-front-end-001)
resource "aws_route53_record" "ditwl-r53-private-front-end-001" {
zone_id = aws_route53_zone.ditwl-r53-private.id
name = aws_instance.ditwl-ec-front-end-001.tags["private_name"]
type = "A"
ttl = "300"
records = [aws_instance.ditwl-ec-front-end-001.private_ip]
}
# Private A DNS Record: Back-end server (ditwl-ec-back-end-123)
resource "aws_route53_record" "ditwl-r53-private-back-end-123" {
zone_id = aws_route53_zone.ditwl-r53-private.id
name = aws_instance.ditwl-ec-back-end-123.tags["private_name"]
type = "A"
ttl = "300"
records = [aws_instance.ditwl-ec-back-end-123.private_ip]
}
# Private A DNS Record: DB Server (ditwl-rds-001)
resource "aws_route53_record" "ditwl-r53-private-rds-001" {
zone_id = aws_route53_zone.ditwl-r53-private.id
name = aws_db_instance.ditwl-rds-001.identifier
type = "CNAME"
ttl = "300"
records = [aws_db_instance.ditwl-rds-001.address]
}
Open a command line shell at the same location where the terraform-aws-tutorial.tf file is located, and, run the Terraform or OpenTofu plan, and apply the commands.
Run tofu plan to generate and review the execution plan. Check each line and value to make sure that it corresponds to the desired change.
Terraform will refresh the state by comparing it with the Cloud resources and produce a plan for the resources that need to be created, updated, or destroyed.
In the past section of the tutorial, some resources were commented out to reduce the infrastructure cost during development. The DNS zones have dependencies with the EC2 instances and the RDS, please uncomment all resources to proceed with the Terraform plan.
Run the Terraform plan:
$ tofu plan
data.aws_ami.ubuntu-23-04-arm64-minimal: Reading...
...
aws_db_instance.ditwl-rds-001: Refreshing state... [id=db-ACRNKG6LHOJHW34OBW3YBTGIVU]
OpenTofu used the selected providers to generate the following execution plan. Resource actions are indicated with the
following symbols:
+ create
OpenTofu will perform the following actions:
# aws_route53_delegation_set.ditwl-r53ds-001 will be created
+ resource "aws_route53_delegation_set" "ditwl-r53ds-001" {
+ arn = (known after apply)
+ id = (known after apply)
+ name_servers = (known after apply)
+ reference_name = "ditwl-r53ds-001"
}
# aws_route53_record.ditwl-r53-private-back-end-123 will be created
+ resource "aws_route53_record" "ditwl-r53-private-back-end-123" {
+ name = "ditwl-ec-back-end-123"
+ records = [
+ "172.21.2.106",
]
+ ttl = 300
+ type = "A"
...
}
# aws_route53_record.ditwl-r53-private-front-end-001 will be created
+ resource "aws_route53_record" "ditwl-r53-private-front-end-001" {
+ name = "ditwl-ec-front-end-001"
+ records = [
+ "172.21.0.174",
]
+ ttl = 300
+ type = "A"
...
}
# aws_route53_record.ditwl-r53-private-rds-001 will be created
+ resource "aws_route53_record" "ditwl-r53-private-rds-001" {
+ name = "ditwl-rds-001"
+ records = [
+ "ditwl-rds-001.crcp5q8td9pz.us-east-1.rds.amazonaws.com",
]
+ ttl = 300
+ type = "CNAME"
}
# aws_route53_record.ditwl-r53-public-front-end-001 will be created
+ resource "aws_route53_record" "ditwl-r53-public-front-end-001" {
+ name = "www"
+ records = [
+ "44.199.183.221",
]
+ ttl = 300
+ type = "A"
}
# aws_route53_zone.ditwl-r53-private will be created
+ resource "aws_route53_zone" "ditwl-r53-private" {
+ name = "demo.itwonderlab.local"
+ tags_all = {
+ "Name" = "ditwl-r53-private"
+ "cost_center" = "marketing-department"
+ "environment" = "pro"
+ "owner" = "IT Wonder Lab"
}
...
}
# aws_route53_zone.ditwl-r53-public will be created
+ resource "aws_route53_zone" "ditwl-r53-public" {
+ name = "demo.itwonderlab.com"
+ tags_all = {
+ "Name" = "ditwl-r53-public"
+ "cost_center" = "marketing-department"
+ "environment" = "pro"
+ "owner" = "IT Wonder Lab"
}
...
}
Plan: 7 to add, 0 to change, 0 to destroy.Run tofu apply to generate and apply the execution plan. OpenTofu will generate a new plan and ask for confirmation before applying the changes. Review the changes and answer yes or no to apply the changes in AWS.
$ tofu apply
aws_key_pair.ditwl-kp-config-user: Refreshing state... [id=ditwl-kp-config-user]
aws_kms_key.ditwl-kms-rds-001-key: Refreshing state... [id=a9925f60-c871-41bd-ba3f-e5a4066c58da]
aws_vpc.ditlw-vpc: Refreshing state... [id=vpc-02b934f2426acc5f1]
data.aws_ami.ubuntu-23-04-arm64-minimal: Reading...
data.aws_ami.ubuntu-23-04-arm64-minimal: Read complete after 1s [id=ami-01eba98c26f317c58]
aws_kms_alias.ditwl-kmsalias-rds-001-key: Refreshing state... [id=alias/ditwl-kms-rds-001-key]
aws_security_group.ditwl-sg-base-ec2: Refreshing state... [id=sg-0e84b8db62b8e0d09]
aws_internet_gateway.ditwl-ig: Refreshing state... [id=igw-0d045eed1d3e2a2b8]
aws_security_group.ditwl-sg-back-end: Refreshing state... [id=sg-04cffe5ba3a4a91ad]
aws_subnet.ditwl-sn-za-pro-pub-00: Refreshing state... [id=subnet-0da274b2ae72deb21]
aws_security_group.ditwl-sg-front-end: Refreshing state... [id=sg-0556ce9da95889d16]
aws_security_group.ditwl-sg-rds-001: Refreshing state... [id=sg-0a2e113b0ab14b423]
aws_route_table.ditwl-rt-priv-zb: Refreshing state... [id=rtb-025ac07e1c24d1e7c]
aws_subnet.ditwl-sn-za-pro-pri-02: Refreshing state... [id=subnet-06185d2fababe83a2]
aws_subnet.ditwl-sn-zb-pro-pub-04: Refreshing state... [id=subnet-0b55d911b7f66e6a6]
aws_subnet.ditwl-sn-zb-pro-pri-06: Refreshing state... [id=subnet-033ae71558502ef32]
aws_route_table.ditwl-rt-priv-za: Refreshing state... [id=rtb-0d5a5f00f57bb8010]
aws_security_group_rule.ditwl-sr-internet-to-ec2-ssh: Refreshing state... [id=sgrule-1652936524]
aws_security_group_rule.ditwl-sr-all-outbund: Refreshing state... [id=sgrule-4250796018]
aws_security_group_rule.ditwl-sr-internet-to-ec2-icmp: Refreshing state... [id=sgrule-4113347279]
aws_security_group_rule.ditwl-sr-back-end-to-db: Refreshing state... [id=sgrule-3209111098]
aws_security_group_rule.ditwl-sr-front-end-to-api: Refreshing state... [id=sgrule-85780268]
aws_security_group_rule.ditwl-sr-internet-to-front-end-http: Refreshing state... [id=sgrule-3488157431]
aws_instance.ditwl-ec-front-end-001: Refreshing state... [id=i-027a11618f6f2ac3e]
aws_route_table.ditwl-rt-pub-main: Refreshing state... [id=rtb-0832c63d2f3fa55b9]
aws_instance.ditwl-ec-back-end-123: Refreshing state... [id=i-079cc3dd35be83128]
aws_route_table_association.ditwl-rta-zb-pro-pri-06: Refreshing state... [id=rtbassoc-028d21a6ba2556f31]
aws_db_subnet_group.ditwl-dbsng-zab-pro-pri: Refreshing state... [id=ditwl-dbsng-zab-pro-pri]
aws_route_table_association.ditwl-rta-za-pro-pri-02: Refreshing state... [id=rtbassoc-047705296475cde67]
aws_main_route_table_association.ditwl-rta-default: Refreshing state... [id=rtbassoc-03cfb8d8b23d3b33a]
aws_db_instance.ditwl-rds-001: Refreshing state... [id=db-ACRNKG6LHOJHW34OBW3YBTGIVU]
OpenTofu used the selected providers to generate the following execution plan. Resource actions are indicated with the
following symbols:
+ create
OpenTofu will perform the following actions:
# aws_route53_delegation_set.ditwl-r53ds-001 will be created
+ resource "aws_route53_delegation_set" "ditwl-r53ds-001" {
+ arn = (known after apply)
+ id = (known after apply)
+ name_servers = (known after apply)
+ reference_name = "ditwl-r53ds-001"
}
# aws_route53_record.ditwl-r53-private-back-end-123 will be created
+ resource "aws_route53_record" "ditwl-r53-private-back-end-123" {
+ allow_overwrite = (known after apply)
+ fqdn = (known after apply)
+ id = (known after apply)
+ name = "ditwl-ec-back-end-123"
+ records = [
+ "172.21.2.106",
]
+ ttl = 300
+ type = "A"
+ zone_id = (known after apply)
}
# aws_route53_record.ditwl-r53-private-front-end-001 will be created
+ resource "aws_route53_record" "ditwl-r53-private-front-end-001" {
+ allow_overwrite = (known after apply)
+ fqdn = (known after apply)
+ id = (known after apply)
+ name = "ditwl-ec-front-end-001"
+ records = [
+ "172.21.0.174",
]
+ ttl = 300
+ type = "A"
+ zone_id = (known after apply)
}
# aws_route53_record.ditwl-r53-private-rds-001 will be created
+ resource "aws_route53_record" "ditwl-r53-private-rds-001" {
+ allow_overwrite = (known after apply)
+ fqdn = (known after apply)
+ id = (known after apply)
+ name = "ditwl-rds-001"
+ records = [
+ "ditwl-rds-001.crcp5q8td9pz.us-east-1.rds.amazonaws.com",
]
+ ttl = 300
+ type = "CNAME"
+ zone_id = (known after apply)
}
# aws_route53_record.ditwl-r53-public-front-end-001 will be created
+ resource "aws_route53_record" "ditwl-r53-public-front-end-001" {
+ allow_overwrite = (known after apply)
+ fqdn = (known after apply)
+ id = (known after apply)
+ name = "www"
+ records = [
+ "44.199.183.221",
]
+ ttl = 300
+ type = "A"
+ zone_id = (known after apply)
}
# aws_route53_zone.ditwl-r53-private will be created
+ resource "aws_route53_zone" "ditwl-r53-private" {
+ arn = (known after apply)
+ comment = "Managed by Terraform"
+ force_destroy = false
+ id = (known after apply)
+ name = "demo.itwonderlab.local"
+ name_servers = (known after apply)
+ primary_name_server = (known after apply)
+ tags = {
+ "Name" = "ditwl-r53-private"
}
+ tags_all = {
+ "Name" = "ditwl-r53-private"
+ "cost_center" = "marketing-department"
+ "environment" = "pro"
+ "owner" = "IT Wonder Lab"
}
+ zone_id = (known after apply)
+ vpc {
+ vpc_id = "vpc-02b934f2426acc5f1"
+ vpc_region = (known after apply)
}
}
# aws_route53_zone.ditwl-r53-public will be created
+ resource "aws_route53_zone" "ditwl-r53-public" {
...
}
Plan: 7 to add, 0 to change, 0 to destroy.
Do you want to perform these actions?
OpenTofu will perform the actions described above.
Only 'yes' will be accepted to approve.
Enter a value: yes
aws_route53_delegation_set.ditwl-r53ds-001: Creating...
aws_route53_zone.ditwl-r53-private: Creating...
aws_route53_delegation_set.ditwl-r53ds-001: Creation complete after 2s [id=N02856711FM6ZWNXWIFGS]
aws_route53_zone.ditwl-r53-public: Creating...
...
aws_route53_zone.ditwl-r53-public: Creation complete after 58s [id=Z059517510UUCSCEZSY0N]
aws_route53_record.ditwl-r53-public-front-end-001: Creating...
aws_route53_zone.ditwl-r53-private: Creation complete after 1m3s [id=Z1002722OPC6CMSA7FBT]
aws_route53_record.ditwl-r53-private-back-end-123: Creating...
aws_route53_record.ditwl-r53-private-rds-001: Creating...
aws_route53_record.ditwl-r53-private-front-end-001: Creating...
...
aws_route53_record.ditwl-r53-private-back-end-123: Creation complete after 12s [id=Z1002722OPC6CMSA7FBT_ditwl-ec-back-end-123_A]
...
aws_route53_record.ditwl-r53-private-front-end-001: Creation complete after 29s [id=Z1002722OPC6CMSA7FBT_ditwl-ec-front-end-001_A]
aws_route53_record.ditwl-r53-private-rds-001: Creation complete after 29s [id=Z1002722OPC6CMSA7FBT_ditwl-rds-001_CNAME]
...
aws_route53_record.ditwl-r53-public-front-end-001: Creation complete after 51s [id=Z059517510UUCSCEZSY0N_www_A]
Apply complete! Resources: 7 added, 0 changed, 0 destroyed.
Review the result, it should be 7 (resource) added, 0 changed, and 0 destroyed.
You can check that the DNS Zone and the Records have been created:
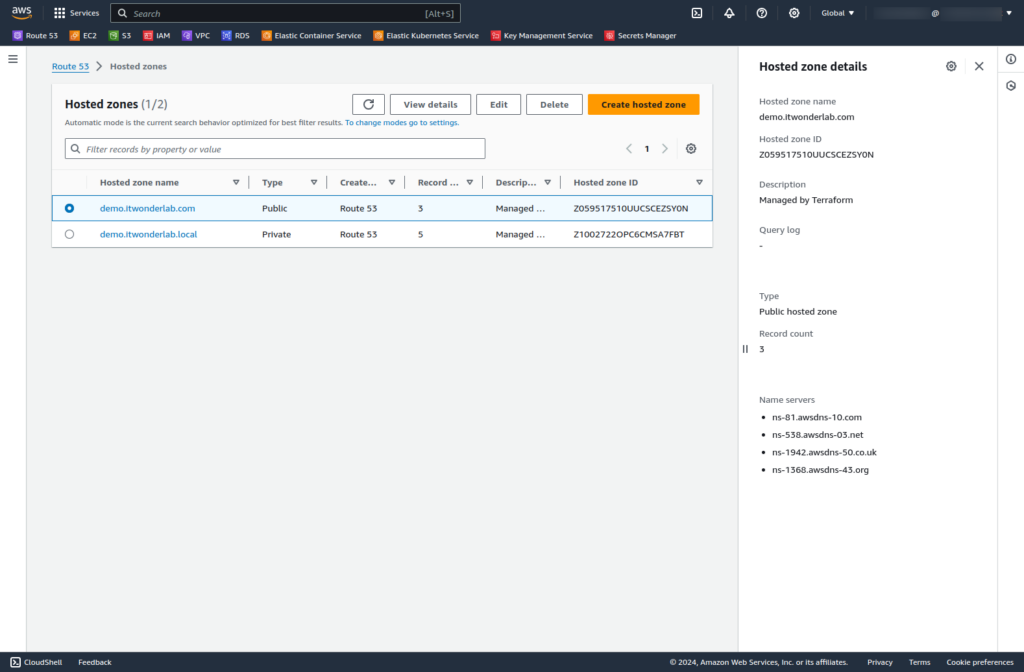
Navigate to AWS Console: Route 53: Hosted zones
The Console shows two DNS Zones, the selected public zone demo.itwonderlab.com has four Authoritivate servers assigned:
The Console shows the DNS Records for the private zone demo.itwonderlab.local, the record ditwl-rds-001.demo.itwonderlab.local is a CNAME (alias) for the AWS assigned FQDN for the RDS database instance access point ditwl-rds-001.crcp5q8td9pz.us-east-1.rds.amazonaws.com:

Instances should use DNS records to reference other instances and databases. AWS will resolve the records to its IPs.
AWS will bill the time that the infrastructure is running. To reduce the cost during Terraform development or when the infrastructure is not needed anymore terraform destroy will be used.
Terraform destroy terminates all the resources created by the plan.
Run tofu destroy to generate and apply the destruction plan. OpenTofu will generate a new plan with the resources to terminate and ask for confirmation before applying the changes.
All data will be lost but you will be able to recreate the infrastructure when needed using tofu apply.
$ tofu destroy .... aws_db_instance.ditwl-rds-001: Still destroying... [id=db-ACRNKG6LHOJHW34OBW3YBTGIVU, 4m10s elapsed] aws_db_instance.ditwl-rds-001: Destruction complete after 4m12s aws_db_subnet_group.ditwl-dbsng-zab-pro-pri: Destroying... [id=ditwl-dbsng-zab-pro-pri] aws_kms_key.ditwl-kms-rds-001-key: Destroying... [id=a9925f60-c871-41bd-ba3f-e5a4066c58da] aws_db_subnet_group.ditwl-dbsng-zab-pro-pri: Destruction complete after 1s aws_subnet.ditwl-sn-za-pro-pri-02: Destroying... [id=subnet-06185d2fababe83a2] aws_subnet.ditwl-sn-zb-pro-pri-06: Destroying... [id=subnet-033ae71558502ef32] aws_kms_key.ditwl-kms-rds-001-key: Destruction complete after 1s aws_subnet.ditwl-sn-zb-pro-pri-06: Destruction complete after 1s aws_subnet.ditwl-sn-za-pro-pri-02: Destruction complete after 2s aws_vpc.ditlw-vpc: Destroying... [id=vpc-02b934f2426acc5f1] aws_vpc.ditlw-vpc: Destruction complete after 2s Destroy complete! Resources: 36 destroyed.
AWS charges for each hosted zone the number of monthly queries to the zone. See Amazon Route 53 pricing for details.
Yes, Terraform supports managing Route 53 health checks and failover configurations using resources aws_route53_health_check and aws_route53_record with failover settings. Define health check settings and associate them with DNS records to enable failover functionality.
Terraform applies changes incrementally, so updating existing DNS records typically doesn't cause downtime. When you make changes to your Terraform configuration and apply them, Terraform will update only the necessary resources without interrupting existing services. For complex migrations review and plan zone and record TTLs.
Private records contain sensitive information related to internal resources within a network, and exposing them in a public DNS zone could pose security risks. Private hosted zones are specifically designed to manage DNS records for internal resources within a Virtual Private Cloud (VPC) or on-premises network connected to AWS using AWS Direct Connect or VPN. These private hosted zones ensure that DNS queries for internal resources are resolved within the private network and are not exposed to the public internet.
Domain registration is a complex process involving different entities, requiring payment and other steps that are better done outside Terraform.
This tutorial series is a work in progress and will have these sections:
AWS with Terraform: The Essential Guide: Sections

IT Wonder Lab tutorials are based on the diverse experience of Javier Ruiz, who founded and bootstrapped a SaaS company in the energy sector. His company, later acquired by a NASDAQ traded company, managed over €2 billion per year of electricity for prominent energy producers across Europe and America. Javier has over 25 years of experience in building and managing IT companies, developing cloud infrastructure, leading cross-functional teams, and transitioning his own company from on-premises, consulting, and custom software development to a successful SaaS model that scaled globally.
Are you looking for cloud automation best practices tailored to your company?